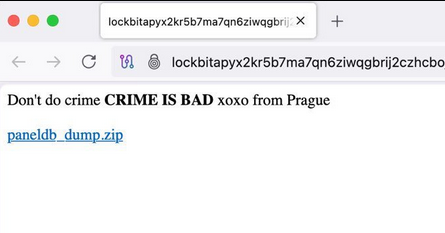
In the following analysis, we will examine the recently leaked database of the LockBit ransomware panel (May 2025), covering all activity from 2024-12-18 through 2025-04-28. The panel was hacked by an unknown actor; the database was dumped, and the interface was defaced.

Since early 2024, leading law enforcement agencies - most notably the U.S. Federal Bureau of Investigation (FBI) and the U.K. National Crime Agency (NCA) - have targeted LockBit’s infrastructure and publicly exposed its leadership. The objective of the article is to provide a better understanding of how Ransomware-as-a-Service (RaaS) operations work, including their weaknesses, in order to implement more effective and efficient lines of defence against such threat actors.
The following analysis is based on the latest LightPanel database leak - please note that it may not include every affiliate active at the date of the breach. LockBit has suffered serious damage to its image over the past few months, resulting in a significant drop in membership. This downward trend was triggered by three major events:



Although some of the investigation’s outcomes may appear amusing, it would be a serious mistake to underestimate the capabilities and resources of LockBit. According to the FBI, LockBitSupp alone made at least $150 million in profits, and the affiliated ransomware operators together made five to ten times that amount. However, keep in mind that, despite these “setbacks”, LockBit is still one of the world’s most powerful ransomware operations.
The following section provides a brief description of the panel’s database structure containing relevant information about the Lockbit operation.
Below is an overview of the database schema. Because LockBit omitted all foreign keys, table relationships can’t be rendered automatically - fields like usersId and adv_id had to be linked manually. Broadly, the tables fall into four areas:
Victims: Contains every detail about each target: company information, chat transcripts, and login records from the chat portal.
Build configurations: Stores everything related to ransomware builds-from the binary itself and its compilation parameters to the embedded public key used for encryption.
Affiliates: Holds affiliate-specific data: account profiles, linked Bitcoin wallets, registration attempts, and user metadata.
Other tables: Miscellaneous or empty tables that play no significant role in operations.

A brief explanation of each non-empty table:
btc_addresses [Payment information, ‘address’ are Bitcoin wallets]

builds [Different ransomware builds for target companies]

builds_configurations [Contains build configurations for the locker]
chats [Chats with victim companies]

clients [Unknown purpose]
files [Paths to compiled ransomware builds]
invites [Affiliate registrations]

migrations [Database migration logs]
news [News for affiliates]
pkeys [Public keys used for encryption]
socket_messages [Unknown purpose]
system_invalid_requests [Logs of invalid panel requests, likely for debugging or simple IDs]
users [User database]
visits [Likely login logs of victims to the ransomware chat]
We will later dive deeper into the btc_addresses, builds_configurations, invites, and users database tables.
The database dump includes hundreds of build configurations, providing deep insight into LockBit’s operation. Both the Linux/ESX and Windows builders share several key features:
self_delete: "1"After execution, the malware binary deletes itself from the filesystem to hinder forensic analysis.
wipe_free_space: "1"Overwrites free disk space to permanently destroy remnants of original files and prevent recovery.
skip_folders: "etc;dev;bin;sbin;usr;var;include;lib;lib64;opt;proc;mbr;tardisks; bootbank;altbootbank;scratch;store;sys;Library;System;boot;snap;.local"Semicolon-separated list of system and virtualization directories excluded from encryption to maintain OS stability and avoid sandbox detection. The exact folders vary between Linux and Windows builds.
userid: 70The userid field contains the account ID of the affiliate responsible for that particular build configuration. This enables law enforcement agencies and security researchers to map each affiliate to the victim organizations they have extorted.
The leak contains several Windows locker configurations. However, few changes have been made since the 2022 builder leak. For a detailed analysis of the Windows builder, see [5] .
Below is a ransomware configuration sample for Linux/ESX platform:
{
"buildModel": {
"id": "1038",
"parent_id": 0,
"status": 100,
"decription_id": null,
"userid": 70,
"stealerid": null,
"key_id": 0,
"comment": "[CENSORED]",
"master_pubkey": null,
"master_privkey": null,
"date": 1744914396,
"company_website": "[CENSORED]",
"crypted_website": "Ta9m8JosJ [CENSORED] HsSQo=",
"revenue": "20kk",
"delete_decryptor": true,
"type": 40,
"max_file_size": null,
"created_at": "2025-04-17 18:26:36"
},
"key": null,
"revenue": "20kk",
"comment": "[CENSORED]",
"company_website": "[CENSORED]",
"kill_processes_list": "",
"folders_to_crypt": "",
"folders_to_crypt_enabled": "0",
"files_to_skip": "",
"files_to_skip_vmdk": "386;adv;ani;bat;bin;cab;cmd;com;cpl;cur;deskthemepack;diagcab;diagcfg;diagpkg;dll;drv;exe;hlp;icl;icns;ico;ics;idx;ldf;lnk;mod;mpa;msc;msp;msstyles;msu;nls;nomedia;ocx;prf;ps1;rom;rtp;scr;shs;spl;sys;theme;themepack;wpx;lock;key;hta;msi;pdb",
"vm_to_skip": "VMwarevCenter;VMware-VirtualSAN-Witness",
"spot_size": "50",
"self_delete": "1",
"wipe_free_space": "1",
"passphrase": "JFG234ASab",
"vmdk_mode": 0,
"wholefile": "0",
"nostop": false,
"nolog": "0",
"extensions": "",
"no_scan_another_dirs": "0",
"skip_folders": "etc;dev;bin;sbin;usr;var;include;lib;lib64;opt;proc;mbr;tardisks;bootbank;altbootbank;scratch;store;sys;Library;System;boot;snap;.local",
"admin_extensions": "vbm;vrb;vbk;vmdk;vlb;vom;vsm;vsb;vab;vdk",
"maximum_logs": "0",
"timeout_enabled": "0",
"timeout": "",
"hidden": "0",
"cvm_ip": "",
"cvm_login": "",
"cvm_port": "",
"cvm_password": "",
"note_show": "0"
}
The inclusion of “snap” directories in skip_folders - which exist on Ubuntu but not on ESX - indicates that the ESX and Linux builds are using the identical ELF binary.
For Windows operating system, LockBit uses a hybrid approach:
The Linux/ESX build, however, shows no embedded public/private key (master_pubkey/master_privkey are null in the leaked configuration) and only a short passphrase. This suggests it may rely purely on symmetric AES encryption with that passphrase-no per-file RSA wrapping of the AES key. Without the full binary, though, this remains an educated guess.
The leaked database contains a total of 76 regular user accounts, including one administrator account and the test user matrix777 - the latter was uniquely identified by sharing the same TOX ID as the admin account. Notably, all user passwords were stored in plaintext, which is surprising considering that Dmitry/LockBitSupp is a security expert.

Each user in the database has a user tag. In the following, we discuss the possible meanings of the different tags. Our interpretation is based on the number of victims attributed to each affiliate, but it should be noted that this is only an assumption based on our observations.
After the U.S. Department of Justice indicted LockBitSupp last year, the group responded to declining membership by publicly opening its affiliate program and slashing the entry fee. The JSON file below lists all 12 Bitcoin addresses generated by the registration panel that received payments. Although the registration process was initiated 3,693 times, Monero was also accepted-making exact attribution difficult. By comparing typical Monero-to-Bitcoin usage rates, we estimate this campaign added only around 20 new affiliates-most of whom, as we will see later in this article, never turned a profit.
[
{
"address": "bc1q6epdl03l005srk65emlnr7tekxxle0vy2xqagr",
"incoming_sats": 770800,
"outgoing_sats": 770800,
"incoming_btc": 0.007708,
"outgoing_btc": 0.007708
},
{
"address": "bc1qd9hr3e0q5z89ryu4n2nrqak2skkdyews07svpw",
"incoming_sats": 829789,
"outgoing_sats": 829789,
"incoming_btc": 0.00829789,
"outgoing_btc": 0.00829789
},
{
"address": "bc1qxg5df29r3e9kqfdxkt9ygeau6yy3mm08zc7gsa",
"incoming_sats": 806400,
"outgoing_sats": 806400,
"incoming_btc": 0.008064,
"outgoing_btc": 0.008064
},
{
"address": "bc1qsdvtnknfummqpw7eh30xwt3en3nc9chtfd8dyz",
"incoming_sats": 852300,
"outgoing_sats": 852300,
"incoming_btc": 0.008523,
"outgoing_btc": 0.008523
},
{
"address": "bc1qewexpdxwkr6xu8tnmlg5fye3z7q4menr7c6m8c",
"incoming_sats": 835000,
"outgoing_sats": 0,
"incoming_btc": 0.00835,
"outgoing_btc": 0.0
},
{
"address": "bc1qv2hgsqdpx84um5epv25l5tlahsyd3dlapnhepp",
"incoming_sats": 818500,
"outgoing_sats": 0,
"incoming_btc": 0.008185,
"outgoing_btc": 0.0
},
{
"address": "bc1qk4ssagl307sjwxqk4pcj4ukndup452j5rxmkej",
"incoming_sats": 720800,
"outgoing_sats": 0,
"incoming_btc": 0.007208,
"outgoing_btc": 0.0
},
{
"address": "bc1q2ukccvdq2nk7t0n802pms345p48emzsqta5w7p",
"incoming_sats": 759700,
"outgoing_sats": 0,
"incoming_btc": 0.007597,
"outgoing_btc": 0.0
},
{
"address": "bc1qecwanftfjseh6qe4sxazh8x0p3f54d85hcvukq",
"incoming_sats": 930000,
"outgoing_sats": 0,
"incoming_btc": 0.0093,
"outgoing_btc": 0.0
},
{
"address": "bc1qgy0tuzle24z7xtn920fd3n37eue2jnp36yn3d2",
"incoming_sats": 895900,
"outgoing_sats": 0,
"incoming_btc": 0.008959,
"outgoing_btc": 0.0
},
{
"address": "bc1quap6ufkkndyfvmeyksc6pn7swz8l2wgaaexpfq",
"incoming_sats": 939300,
"outgoing_sats": 0,
"incoming_btc": 0.009393,
"outgoing_btc": 0.0
},
{
"address": "bc1q8jnjgppawydxy6t2fh9k8kjgm4llu7dm03qla7",
"incoming_sats": 877800,
"outgoing_sats": 0,
"incoming_btc": 0.008778,
"outgoing_btc": 0.0
}
]
To understand revenue flows, we first mapped the advid field in the btc_addresses table to the corresponding id in
the users table, linking each affiliate to their generated Bitcoin wallet. We then retrieved the total historical
inflows for each address and checked current balances on-chain.
The current balance of each wallet represents the share of ransom payments that goes directly to LockBitSupp (Dmitry), while the remainder to date reflects the affiliate’s profit.
Surprisingly, only two affiliates still generate significant revenue - their wallets hold the bulk of payments - while the other ten appear to have generated negligible returns, suggesting they have defected to competing ransomware groups.

This highlights that two affiliates (Swan and Christopher) account for over 97% of tracked revenue, while the rest have negligible earnings.
| Affiliate | Revenue (EUR) (2025-05-19) | Revenue (BTC) | % of Total |
|---|---|---|---|
| Swan | €2 072 629.48 | 22.6293 | 87.0 % |
| Christopher | €251 527.66 | 2.7480 | 10.6 % |
| umarbishop47 | €27 264.35 | 0.2974 | 1.1 % |
| PiotrBond | €10 714.97 | 0.1172 | 0.4 % |
| ArrynBaird | €8 695.52 | 0.0951 | 0.4 % |
| Iofikdis | €6 325.13 | 0.0690 | 0.3 % |
| Brown | €3 393.43 | 0.0371 | 0.1 % |
| btcdrugdealer | €2 133.71 | 0.0233 | 0.1 % |
| JamesCraig | €1 558.49 | 0.0170 | 0.1 % |
| Dezed941 | €5.84 | 0.00006 | 0.0 % |
The affiliate revenue distribution is highly skewed: two top performers (Swan and Christopher) account for nearly 98% of all tracked earnings, while the remaining eight affiliates collectively contribute just 2.4%. Despite lowering the registration fee from $20.000 to $777, most new affiliates have failed to generate meaningful returns - several made less than €5,000. This suggests that LockBit’s affiliate program has become concentrated around a small core of professional actors, with the majority either inexperienced or diverted to competing operations. Going forward, defenders can prioritize targeting these high-value affiliates and their infrastructure to disrupt the bulk of LockBit’s revenue stream.
Caveat: It is possible that other, higher-ranking panels still exist and have not been compromised, so some profitable partners may be working in secret.
If you need the bitcoin addresses from the database dump as a basis for further investigation, please refer to:
This can, for example, be used to trace the funds post-extortion to attempt to identify the affiliates.
The LockBit LightPanel breach offers a rare, comprehensive glimpse into one of the world’s most prolific ransomware operations. From the panel’s doxxing and server seizures to the leaked build configurations and user database, we’ve seen how LockBit’s infrastructure and affiliate program function - and where they’ve faltered. The Linux/ESX builds suggest a simpler symmetric-encryption scheme, diverging from the Windows hybrid RSA/ECC-AES model. The user database revealed poor security hygiene (plain-text passwords), a shrinking membership base, and an affiliate hierarchy dominated by “newbies” and a handful of high performers. Blockchain forensics confirmed that two affiliates generate virtually all tracked Bitcoin revenue, while most others earn next to nothing.
To close this blog post, we want to echo the sentiment recently expressed by VX-Underground’s Smelly, as it captures the current situation quite well:
After the FBI and NCA UK took down Lockbit ransomware group servers, arrested their lead developer, sanctioned the group, and listed the “leader” of the group on the FBI’s Most Wanted, we assumed Lockbit ransomware group would either rebrand or die.
Well, they died for a little. But we are beginning to see signs of Lockbit ransomware group again. The past few weeks we have seen more and more reports surface of their attacks. Although they are no longer near where they used to be ( 30+ ransoms a day), the fact they’re making a comeback is both impressive and scary.
Lockbit ransomware group is like a cockroach. He is immune to virtually everything - we thought he was dead, but he is alive still.

[1] LockBit attempts to stay afloat with a new version, Trend Micro (2024), Available at:
https://www.trendmicro.com/en_us/research/24/b/lockbit-attempts-to-stay-afloat-with-a-new-version.html
[2] Law enforcement disrupts the world’s biggest ransomware operation, Europol (2024), Available at:
https://www.europol.europa.eu/media-press/newsroom/news/law-enforcement-disrupt-worlds-biggest-ransomware-operation
[3] Treasury sanctions administrator of LockBit ransomware operation, US Department of the Treasury (2024), Available at:
https://home.treasury.gov/news/press-releases/jy2326
[4] Transnational Organized Crime Rewards Program – LockBit ransomware administrator Dmitry Yuryevich Khoroshev, US Department of State (2024), Available at:
https://www.state.gov/transnational-organized-crime-rewards-program-2/lockbit-ransomware-administrator-dmitry-yuryevich-khoroshev/
[5] Research opportunities on tools leaked from TAs, SecureList, Available at:
https://securelist.com/lockbit-ransomware-builder-analysis/110370/